[breadcrumb]
 Register for a webinar and qualify for a free switch, firewall or WAP!
"
Register for a webinar and qualify for a free switch, firewall or WAP!
"
Firewall or Security Appliance?
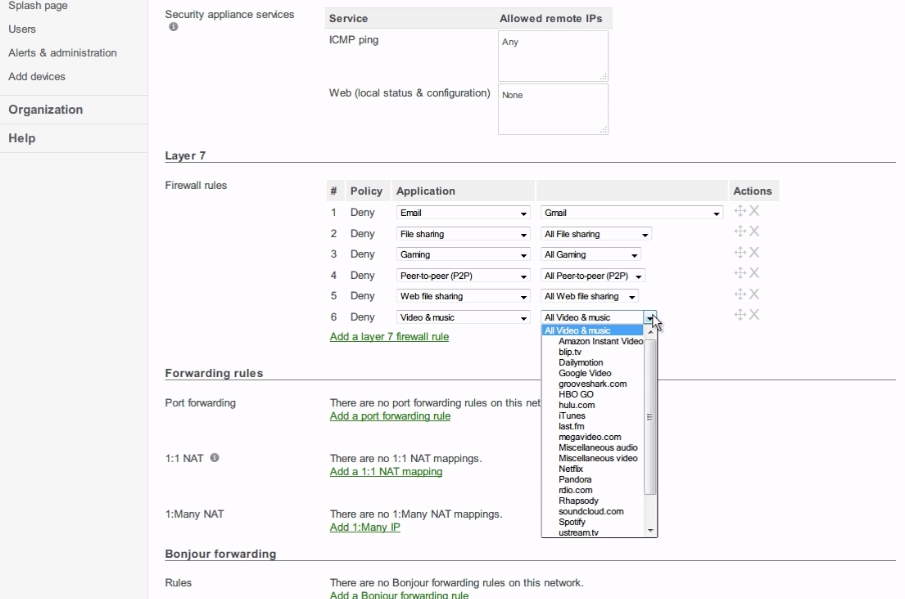
Along with the general tend for business to move to a subscription based, recurring revenue model, the ubiquitous firewall has also moved to the cloud! In the case of the firewall, however, there is measurable and dynamic benefit to be realized by coupling your firewall to a cloud based subscription. The "wild west" that characterizes the internet in the 21st century demands a dynamic, self healing, unified treat management strategy! It is no longer acceptable to use simple statefull packet inspection based firewalls that limit activity based on network layer source and destination IP address matching. Firewalls must now become "security appliance" solutions! Content Filtering Intrusion detection and prevention and a growing shared database of malware protection with cross referenced "reputation" based real time analysis is now the minimum daily adult requirement for network Internet work security. Most of the popular firewalls in the commercial market place now couple some form of a subscription service to the base cost of the actual hardware. Generally these subscriptions are spam and email filtering solutions at the low end, but include very advanced content filtering and malware protection at the high end. Effective content filtering and malware protection requires access to a ever growing database where global information about daily treat and reputation analysis can be analyzed and shared among subscribers. Identity based networking is also an essential component in managing network resource access. Group policies that limit the facilities that the "guest" wireless network can access and the bandwidth that it can use, from the facilities and bandwidth that the corporate user can access begin to define the minimum specification for network computing.Meet My Meraki!
We are particularly fond of the Meraki solution as a good fit alongside of the more sophisticated CISCO Next Generation and "SourceFire" solutions. Both technologies are recent CISCO acquisitions and significantly expand the company's well established range of threat management, Identity and VPN solutions. The Meraki products are not only subscription based, but are truly "cloud" resident. This makes it very attractive for IT teams or Managed Service Providers to remotely install, configure and monitor geographically distributed firewalls and VPN devices. When coupled with the subscriptions for ongoing software updates, the system provides unparalleled cost/benefit performance in the following key areas:- Identity Based Access and User Group Policy Control - Local or Active Directory definition of users and guest
- Intrusion Prevention - Active before, during and after monitoring of known treats
- VPN Automation - Mesh or Hub and Spoke configurations to integrate remote offices and work groups
- Content Filtering - Limit internet access by specif URL or Group like "peer to peer", "file sharing" or "Social Media".
- Anti Malware and Anti Phishing - Active scanning of all HTTP traffic
- High Availability and Fail over - Device and connection security through multiple uplinks
- Application Visibility and Control - Know exactly who is using what and how much!
- Centralized Management - Log into the device through your cloud based "dashboard
