You too can have an exciting career in CyberSecurity!
After a 40+ year career in information technology with a core competency in integrated voice and data networking, I developed an interest in learning Cybersecurity. My knowledge of the subject was tangential resulting from my experiences as a CISCO brat, earning certifications in Switching, routing, Security, collaboration and wireless along with cloud certification from AWS. I do have a BS granted back when vacuum tubes were still part of the computer science curriculum, and I still remember Fortran and Cobol being my basis for learning C from my hero’s Kerrigan and Ritchie. For me life is a continuous learning experience, gaining knowledge, skills and keeping abreast of the rapidly changing technology as we moved from twisted copper pairs, to packet switched networking.
Imagine my surprise when I discovered that you could become a “hacker” by watching YouTube videos and wearing a Guy Fawkes mask while donning a black hoodie and giving yourself a a kool hacker name! Apparently, you can skip all the basics and move directly to a career as a pen tester working in a “SOC” making more money than the hackers planting Ransomware! Just download Kalie Linux or Parrot OS and off you go! Enter a few Linux commands and presto, you are an “ethical hacker”.
An Industry is Born!
In fact an entire industry has materialized selling this dream to a generation raised on Mr. Robot videos! It is astonishing the number of “schools” subsidizing this dream! Some schools even create their own “certifications” to attest to your newly acquired “ethical hacking” skills. The fact that you have no background in operating systems, networking, security, programming or software engineering matters little, after all you are a “Certified White -Hat-Hacker”!
One such “school” is operated by a self-proclaimed “Master OTW” who is rumored to be a world famous hacker. Not only a world famous hacker but the most famous hacker, with no apology to Kevin Mitnick! His exploits are so infamous that he has to hide his true identity for fear of retribution from Russians and other nation state actors who have been victimized by his prowess as a hacker! Along with hiding his identity, he is also hiding any way of validating his many claims including that of being a former College Professor and a sought after consultant to the three letter intelligence agencies and the US Military.
Want to Audit a “Master OTW” Class?
I was sucked in by the “Master OTW” hype and I signed up to “learn from someone who was actually hacking”! There is an old adage: “you never get a second chance to make a first impression”. In September of 2022 I was apparently an early subscriber as it was clear that OTW did not have the act together yet. I was caught between the various subscription levels that he was apparently still hammering out. I went back and forth with him in email several times to get things squared away. I also noted a link between “hackers-arise” and a new certification offering. In one email exchange I asked “Master OTW” point blank if he was the owner of WhiteHat-Hacker.com or if he had an equity position in that venture. He refused to answer me and my BS meter started to move toward red alert. (Thanks to the wayback machine the original White-Hat-Hacker site is still visible, but has now been made “respectable” by yet another organization).
Why re-invent the wheel?
After attending one of his online “instructor” led classes, I was astonished at just how poorly prepared this world famous hacker was! Every YouTuber (offering yet another “script kiddie” presentation on how to setup a reverse shell using NetCat between two computers on a private network), offers up a disclaimer that this presentation is for educational purposes only and should never be executed on a computer you do not have permission to hack! Yet “Master OTW” was demonstrating hacking devices for which he had no permission. In clear violation of US Law regarding private citizens working with foreign governments, he was absolutely giddy hacking cameras in Ukraine to “spy on Putin” and inviting all to join him in his attack of critical infrastructure in Russia, (The Computer Fraud and Abuse Act (CFAA) is a U.S. federal law that criminalizes certain activities involving unauthorized access to computers. It applies to US citizens, even if the hacking activities are conducted outside of the US).
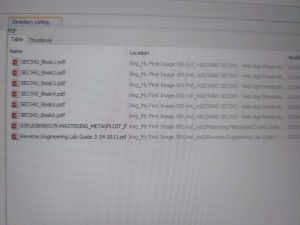
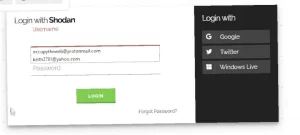
His slides are in large part plagiarized from other schools like SANS. For a cybersecurity guru, the “Master” often exposed materials during his presentation that underlined his arrogance and complete lack of caution or copyright. For example, when opening files on his computer, live on the internet, you could see that they were copied (exfiltrated?) from SANS. Often he would leave an API key exposed which was easily copied.
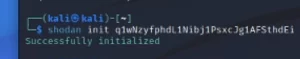
(Above, one image is of Shodan API Key, the other image is a screen shot of “Master OTW” laptop file search showing SANS files of class materials used by “hackers-arise”. Some images here are distorted on purpose.)


( Similar or plagiarized content / occupytheweb27 )?
He also has a speech pattern that drove me completely crazy! Almost every sentence ended with the word “ok” as if it were a punctuation mark. Occasionally, an “alright” but I once counted the number of times he said “ok” in one presentation only to give up after the first 100 utterances.
After boring his audience by reading the plagiarized slides line by line, he often bumbles his way through his computer demonstrations. He continually fails to “sudo” and has to revise every command line entry. (This from the author of Linux Basics for Hackers). The commands never work, and it is obvious he does not take the time to rehearse or prepare his presentation materials and demonstrations. Many times, it is a student that corrects him and gets the presentation back on track.
The Question: who is “Master OTW”? Hackers-Arise?
I noted in one presentation that he was apparently on StarLink with an IP that terminated in Utah/Montana! In several of his classes, you can note wifi networks that surround him (Hughs, Mandella, Magic Cabin, etc,) and using WiggleNet you are able to confirm his general location in both Bozeman and Salt Lake. So if “Master OTW” , who for the small sum of $79 will teach you how to be anonymous online, was that careless I determine to find out his true identity. After all, as an aspiring “hacker” I had to learn how to make use of OSINT and this was a great opportunity to do just that!
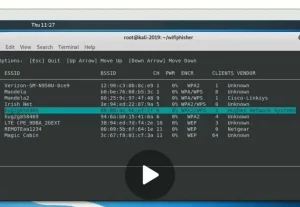
(Don’t try to play the video, it is a screen shot from one of his videos)
Having paid for the class subscription using PayPal, I noted that the transaction was recorded as billed by “hackers-arise”. This was the first step in my investigation. Unfortunately, that was most likely a dba and how the money moved from PayPal to “Master OTW” was not immediately apparent. I asked for either a 1099 or a receipt but one was never provided. (I did report the $1500 payment on my IRS return and sent a 1099 to “hackers-arise”, a non existent company.).
Again, he is either arrogant or he is sloppy as his on screen live presentations left all kinds of clues, and one individual name repeatedly showed up! In one of his demo’s while logging into Shodan, his cache was exposed His class material is videoed and online but he does not even take the time to edit out the errors. I remain thankful for the ability to fast forward through these painful sessions as most of his classes that take three days can be edited down to less than one day! (#DavidBombal and #JohnHammon have nothing to worry about).
(from Ip Camera Hacking Day 2.3 12 min. and 2 sec)
These are screen shots from recordings on his site, or from live online class presentations. You can see a login name that is regularly turning up when you interact with “Master OTW”, Kieth2781@yahoo.com (the key name “Keith” is the subject of further study). In one class he actually left the account key for his online store clearly visible on the screen!
(In fairness, I will not publish it nor his phone number and home address, which if this “student” can find it, so can the Russians!)
Doing a memory dump on one file he himself provided along with a virtual machine image that the class was told to download, we once again find “Keith” this time with the email address. (Keith.Debus)!
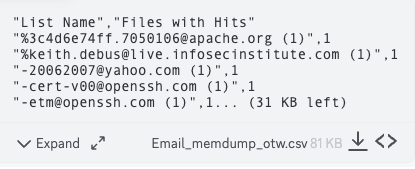
“List Name”,”Files with Hits” “%3c4d6e74ff.7050106@apache.org (1)”,1 “%keith.debus@live.infosecinstitute.com (1)”,1 “-20062007@yahoo.com (1)”,1 “-cert-v00@openssh.com (1)”,1 “-etm@openssh.com (1)”,1… (31 KB left)
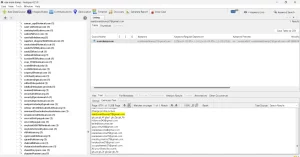
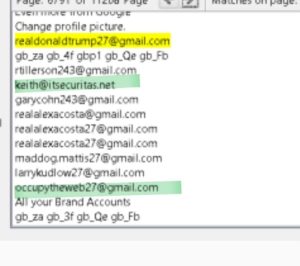
In many of his demo’s he is logged in as “K”, not sure what that means? Keith? (could the worlds most famous hacker be that careless)?
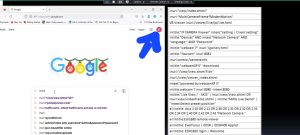
I also noted that “OTW” in one form or another showed up as an email address for that individual, usually as a gmail account not the protonmail account “Master OTW” later adopted. I found that individual on Linkedin, Twitter and Reddit along with other versions of the OTW email format.

![]()
This was interesting but the best was yet to come!
Using the usual search tools, a bit of google dorking, whois and the wonderful archives at the “way back machine”, I was beginning to develop a hypothesis. I remembered back in the day when I was leaning to write SNORT rules, there was a “school” named snort-training.com and thanks to the wayback machine I found this gem!

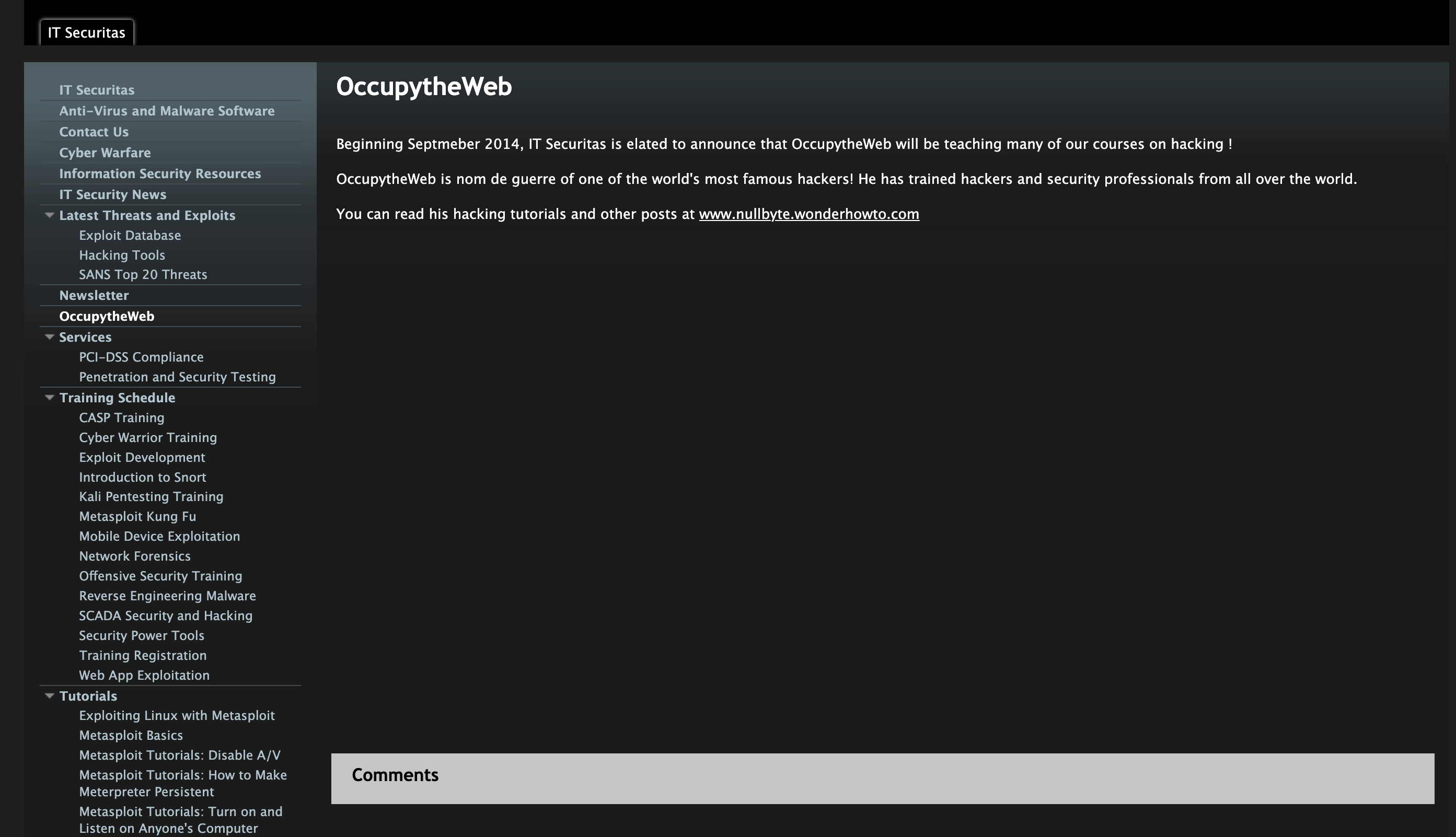
It was a short step to identify the owner of the snort-training.com operation as Keith DeBus. Keith shares many of the very same claims made by “Master OTW”, for example, read his biography. If they are not the same person, then this is just other example of the “Master OTW” plagiarizing content.
 “Keith DeBus is a former professor of computer science with over 20 years of IT experience. He is now the President of IT Securitas (www.itsecuritas.net), a leading IT security and pen-testing firm. He has published numerous articles on cyber security, penetration testing, digital forensics and cyber warfare. DeBus has trained personnel from every branch of the U.S. military (Army, Air Force, Navy) and personnel from the NSA, CIA, FBI and NCIS in cyber warfare tactics.
“Keith DeBus is a former professor of computer science with over 20 years of IT experience. He is now the President of IT Securitas (www.itsecuritas.net), a leading IT security and pen-testing firm. He has published numerous articles on cyber security, penetration testing, digital forensics and cyber warfare. DeBus has trained personnel from every branch of the U.S. military (Army, Air Force, Navy) and personnel from the NSA, CIA, FBI and NCIS in cyber warfare tactics.
DeBus is an internationally recognized expert on cyber warfare, network “hacking” and network intrusion detection systems (NIDS). Mr. DeBus holds or has held the following IT certifications; Sec+, CEH, CPT, ECSA/LPT, CHFI, CISA, CISM and CISSP”
This does not mean Keith is in fact, “Master OTW” but they clearly know each other. Interestingly enough, itsecuritas, now defunct, has also disappeared but not before reporting that “Master OTW” would be taking over! (Note the similar course content).
The photo seems to be taken at the same time that this youtube video, made some 11 years ago and yet has over 192 views! For some real fun, run the voice of Keith and the voice of “Master OTW” through your favorite voice analytics tool (2).
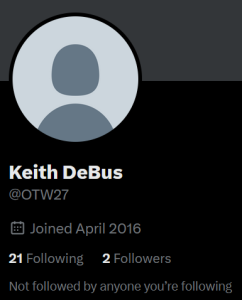
Keith’ Linkedin profile, however, shows none of the certifications that he claims in his profile. No references, no credentials, no job history. In another public record search we note he was in Michigan, where other information suggest he earned a BA degree.
(Wonder why Keith suddenly deleted his video after all these years? Fortunately we have another):
He never claimed to be a great business man!

Keith who seems to bounce between Utah and Montana, has had a troubled, unsucessful and often a difficult life. His past is checkered with an unfortunate divorce, bankruptcy, many failed businesses most of which are “schools” and some criminal entaglements that might cause someone to hide their identity. In 1999 Keith Debus, was charged by information filed in the District Court for the Eighteenth Judicial District in Gallatin County with felony theft by stockholders in one of his ventures, found guilty and was incarcerated (see mug shot). To be fair, this was set aside in 2002 because of a technicality in the case proceedings.
His criminal record, according to Intelius and other public records, appears to include everything from motor vehicle infractions to communications fraud, and receiving stolen materials. This is a story reported by Salt Lake Tribune 4/15/2009: Fugitive commodities trader Keith H. Debus was arrested by the FBI in Salt Lake City on Wednesday morning. Debus, who is facing charges in New Mexico for allegedly defrauding a Sante Fe woman of $25,000 in a commodities trading scheme, is being held without bail in the Salt Lake County Jail.
Fugitive Commodties Trader nabbed by FBI in Salt Lake City.

Utah man pleads guilty to scamming NM woman
Virtual Computer’s owner gets jail time
Keith has a list of failed or delisted companies in which he was the owner, officer or director:
- IT Securitas 1/2011 – (last filing 12/23)
- Team Virtual 12/20 / 11/23 Last Filing
- Virtual Computer Technology April( March 1994)
- VCT INC incorporated 4/2018 – 11/2023
- PrimeMedia Inc. 4/2018 – 11/2023
- BioMetallics Inc. 4/2018 – 11/2023
- Drexel Financial Group 11/2015 – 7/2004
- Tools for Design 7/2003 – 11/2015
- President Laocoon Capital Research 10/2008
- (Virtual CIO is in here some place)
The Cybersecurity Industry needs new leadership!
 Whatever the case with “Master OTW” whomever he might be, the secrecy and inability to substantiate credentials is in my opinion, characteristic of people who have something to hide. Why not take all those credentials you boast of and make them verifiable? As JFK once warned us, secrecy is a despicable and an unnecessary practice. (I myself go by the moniker DrVoIP, but Google me and you will view my entire life)!
Whatever the case with “Master OTW” whomever he might be, the secrecy and inability to substantiate credentials is in my opinion, characteristic of people who have something to hide. Why not take all those credentials you boast of and make them verifiable? As JFK once warned us, secrecy is a despicable and an unnecessary practice. (I myself go by the moniker DrVoIP, but Google me and you will view my entire life)!
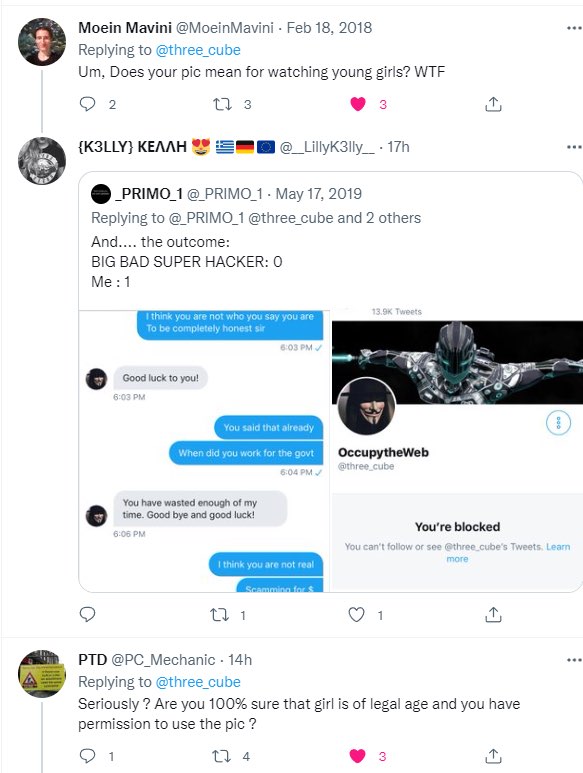
In my opinion “Master OTW” may be a great hacker, but my experience as his student, has not been encouraging or supportive. He does not tolerate criticism and has banned anyone who is critical of his work. After paying $1500 for a subscription you can easily find yourself banded from the site and no longer allowed to participate in the Discord community for the “school”and your money will not be returned! You will have little recourse as “Master OTW” and “hackers-arise” is a marketing fiction. Drop the mask and lets bring some professionalism to this industry!
(UPDATE 1/18/24)
Since publishing this blog, “Master OTW” has banned me from my three year paid subscription to “Hackers-Arise” and refuses to refund the payment. I offered to drop the entire matter if he returned my $1500. Any business man would have evaluated this situation and concluded that returning the money would be the least cost resolution. He said “sue me” and “see you in court”. As he continues to hide behind his DBA, this is a taught as childish as “catch me if you can”. One wonders how the money to “Hackers-Arise” flows back to “Master OTW”.
Several students have contacted me with similar stories about being banned and having their payments held. One student shared his concern that a complex password he used only on Hackers-Arise, was now being used elsewhere along with his credit card information. One thing is obvious, “Master OTW” has the business ethics of a “silk road” drug supplier. He conducts himself like a spurned teenage girl. There are no “terms of service” or contracts, so proceed with caution.
Watch this space for updates as we have no intention of letting ‘Master OTW’ continue to rip off students.
(UPDATED 1/20/24)
It seems that Keith is deleting files. He recently deleted the YouTube video we identified for your consideration.
(Updated 2/5/24)
We now have his home address and SS#. OTW when you least expect it, expect it! Process server! (or just credit the $1500)!
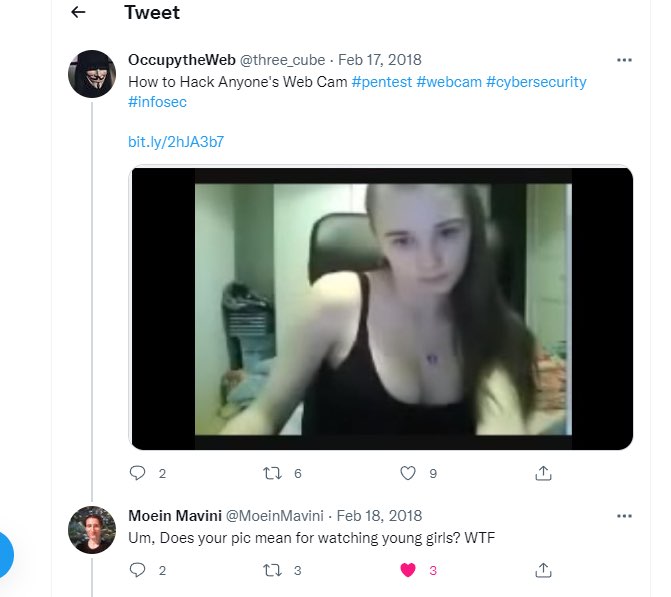
update 9/28/24
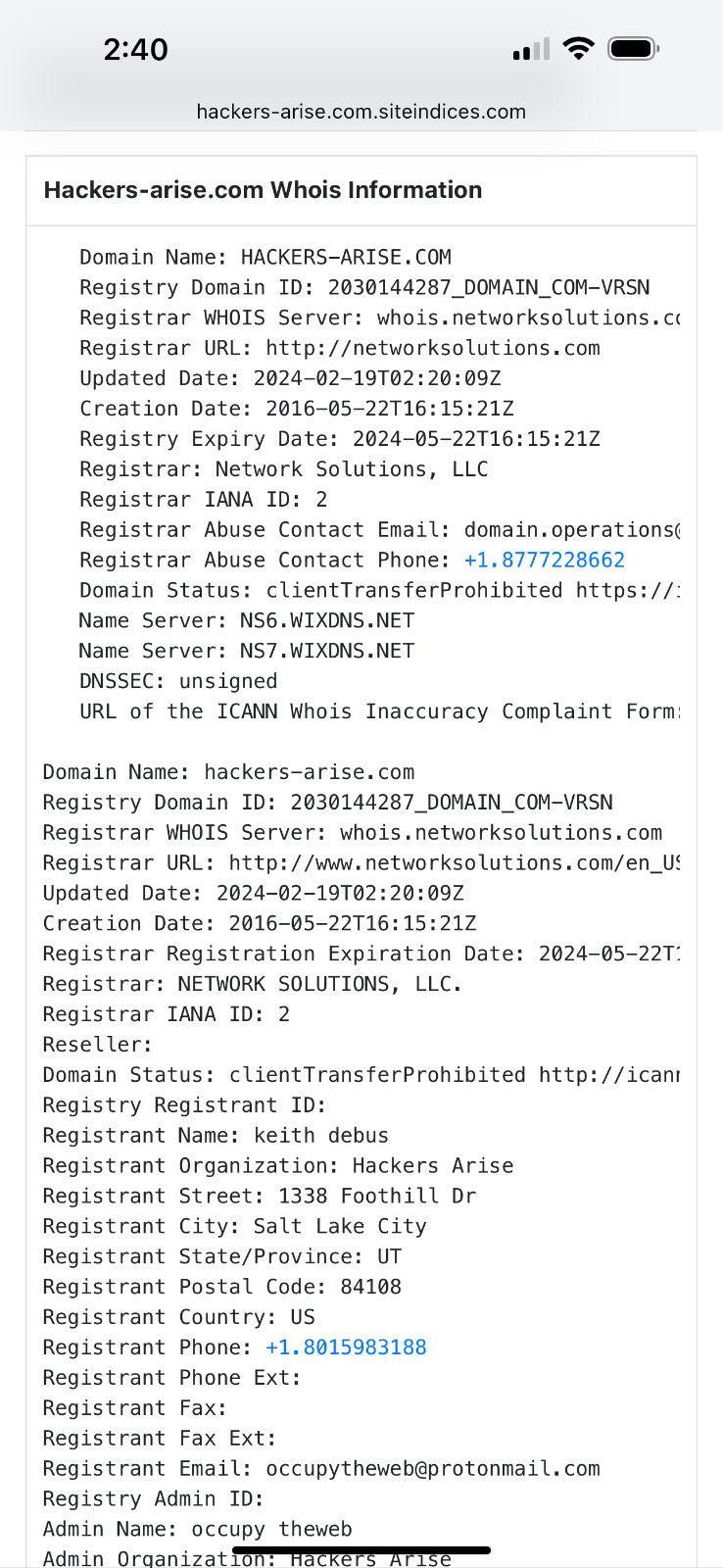
update 1/28/25. White Hat Hacker Certification? Yet another OTW scam?
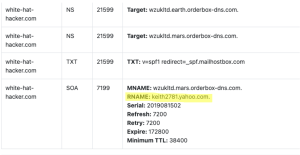
What could be better that starting your own school and issuing your own certifications?
Check out this link https://white-hat-hacker.com.siteindices.com. and note the RNAM? Recognize it?
update 8/1/25
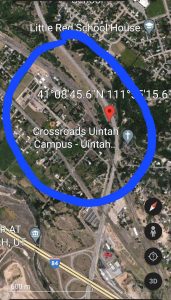
The Greatest Hacker in the World continues to expose his careless arrogance and stupidity. During a recent presentation on “locating the position of a wifi AP”, written by one of his students, he once again exposed his location. During the demo, he listed local Wifi AP SSID, including his own:
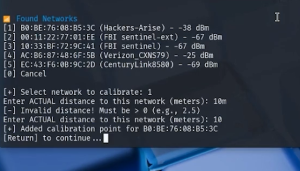 and then it was a simple search to get the geolocation:
and then it was a simple search to get the geolocation:
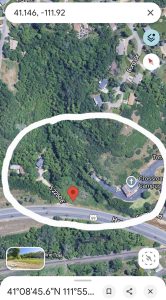
CLICK TO ENLARGE – Even though one WiFi is marked Hackers-Arise, the AC:86:87:48:6F:5B (Verizon_CXNS79) -In this case, -25 dBm basically means “a few meters away” or even in the same room. Students report they can even hear the Church Bells ringing in the background!
For serious students, seeking professional guidance and credentials from accredited resources, check out these free classes!
The world of Cybersecurity is an exciting world and I encourage those who have a serious interest in the art and science of this competency to pursue a more traditional program of learning. There are many absolutely free classes taught by the top vendors and universities on the planet including Harvard, MIT , Google and CISCO to name a few. (Do you really think OTW could pass the CISCO 350-201 CCNP in Cybersecurity) Do not be sucked in by YouTube videos and fly by night schools with no legitimate credential or history.
Cisco Networking Academy is offering this Certifications and Courses (FREE)
- Introduction to Cybersecurity
https://netacad.com/courses/cybersecurity/introduction-cybersecurity… - Cybersecurity Essentials
https://netacad.com/courses/cybersecurity/cybersecurity-essentials… - Networking Essentials
https://netacad.com/courses/networking/networking-essentials
???? ????????????? ??????? ???? ??????:
- Learn programming with JavaScript https://learndigital.withgoogle.com/digitalgarage/course/learn-programming-with-javascript…
- Google’s Python Class https://developers.google.com/edu/python
- Machine Learning Crash Course https://learndigital.withgoogle.com/digitalunlocked/course/machine-learning-crash-course…
- Fundamentals of Digital Marketing https://learndigital.withgoogle.com/digitalgarage/course/digital-marketing…
- Introduction to Baseline: Data, ML, AI https://cloudskillsboost.google/quests/34
Introduction to Computer Science
- CS 50 – Introduction to Computer Science, Harvard University (cs50.tv)
- CSE 142 Computer Programming I (Java Programming), Spring 2016 – University of Washington
- CS 1301 Intro to computing – Gatech
- CS 106A – Programming Methodology, Stanford University (Lecture Videos)
- CS 106B – Programming Abstractions, Stanford University (Lecture Videos)
- CS 106L – Standard C++ Programming(Lecture Videos)
- CS 106X – Programming Abstractions in C++ (Lecture Videos)
- Programming in C++ – IIT Kharagpur
- Python Boot Camp Fall 2016 – Berkeley Institute for Data Science (BIDS)
- Modern C++ Course (2018) – Bonn University
- Modern C++ (Lecture & Tutorials, 2020, Vizzo & Stachniss) – University of Bonn
Notes –
1 – The information presented in the blog are either from databases available to the public, “hackers-arise” student materials I paid for, or from my personal interaction with the subject matter. Any opinions expressed are my own!
2 – Auditory Analysis is a method of voice comparison where a practitioner listens to the questioned- and known-speaker’s recordings and compares the voice properties (vocabulary choice, pronunciation of particular words and phrases, segmental pronunciation, intonation patterns, stress patterns, speaking rate, etc.) to determine how much more likely it is that these recordings belong to the same speaker than to different speakers.
3 – We get ongoing reports from students none of which have caused us to change our mind about the “worlds most famous hacker”!
#OTW #hackers-arise #hackersarise #occupytheweb #infosec #cybersecurity #OccupytheWeb #three_cube #@three_cube, White-Hat-Hacker,

