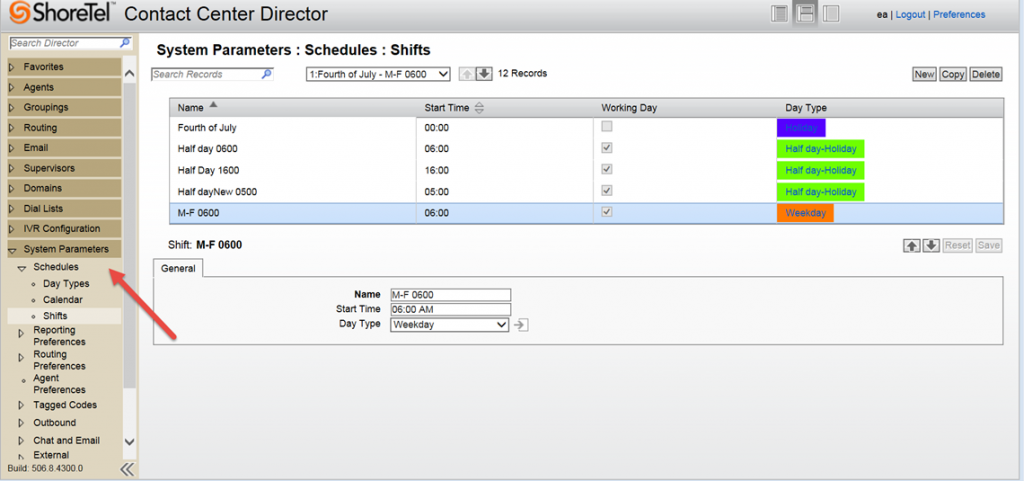
Why use Shifts at all?
Most call centers have “on hours” and “off hours” that route callers to different options based on time of day and day of week. ShoreTel ECC has a concept entitled SHIFTS. Shifts have day types: Weekday, Weekend and Holiday. You go to System Parameters in the Contact Center Director, then Schedules and the create a Shift. Name the Shift something useful, specific the day type and the time the shift action should occur. You then apply it to the IRN you want to alter, open or close based on your shift schedule. If you do not understand shifts, however and how they are utilized by the ECC you are at risk of shutting down your call center unintentionally.
Let’s take a closer look at how Shifts work!
Each IRN in the ECC that uses Shifts, has a default setting that specifies where the call should route, if there is no corresponding shift instruction. The Shift might specify a Script, Service or Device. For example you might have Shift named “M-F” defined for day type Weekdays that is active at 8:00AM and specifies that the call should be routed to a script for handling calls during “on hours”. You might then also add another Shift named “Lunch” for a day type Weekdays and set if to activate at 11:59 AM and point it to script that plays an announcement alerting callers that the call center is closed for lunch and invites them to call back at 1PM (never happen but it makes for a good lesson example). Now we create another Shift also named “M-F” for day type Weekday and set it to activate at 1PM. This action points the calls back to the script for “on hours”. Clearly, you also created a Shift for “M-F” for day types Weekday and set the action time at 5PM. The action is to send the call to the script for After hours. Make sense? Seem easy?
Danger – The trouble Spot with Shifts!
Let’s assume you have an IRN for Sales and an IRN for Technical Support and you apply the shifts we defined above, to both IRN’s, but on the sales IRN they do not close for lunch! For this reason, you do not apply the Shift entitled “Lunch” to the Sales IRN. Let’s assume the default route for the Sales IRN is the Closes script, so that after hours calls defaul if not specified in the Shift list to the after hours call handling. So what do you think will happen to the Sales IRN at 11:59?
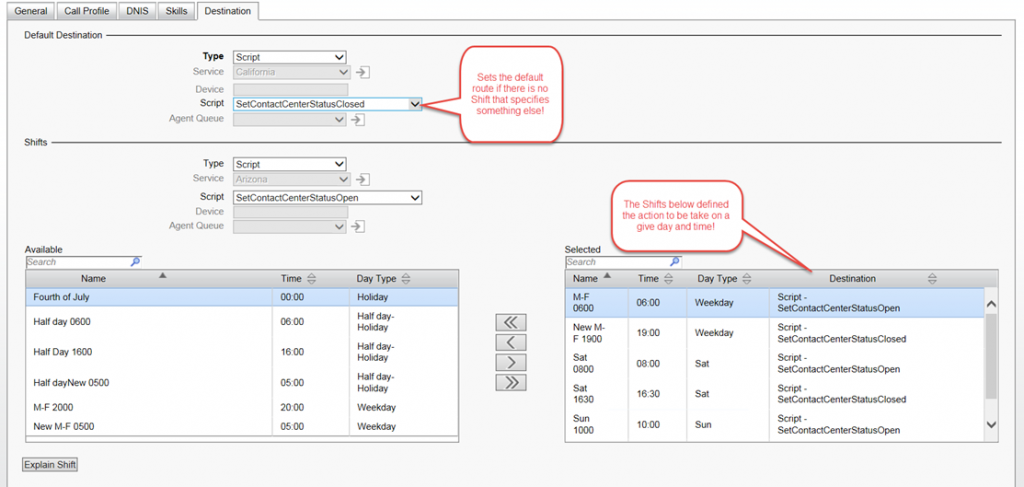
The fact that you created a Shift and one now exists for “Lunch” during the week is the important take away. Once you apply Shifts to an IRN, ALL shifts apply even if you did not apply that shift to your IRN. In this simple example, the Sales IRN will follow the Default route because you did not specific an alternative destination in you shift list on the Sales IRN for Lunch time. The fact that the Shift exists in the ECC database, requires that you specify an action for that Shift! This is where most folks get into trouble!
What Version of ECC is your Shift definition?
In versions before Connect and ECC 8, Shifts required you to open and close a shift. After version 8, you are not required to close a shift but it would be a good practice to do so! You must account for all shifts, even if they are to relevant to your IRN. The only way around this is to NOT apply any Shifts to an IRN. If the IRN does not use Shifts at all, it will ignore all Shifts! A bit confusing but once you “get it” it is easy.
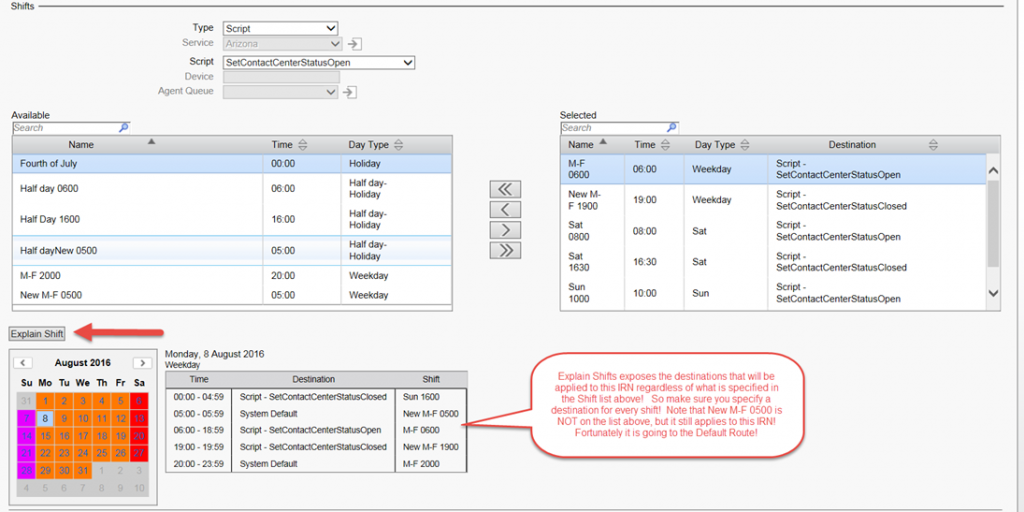
When in Doubt press Explain Shifts!
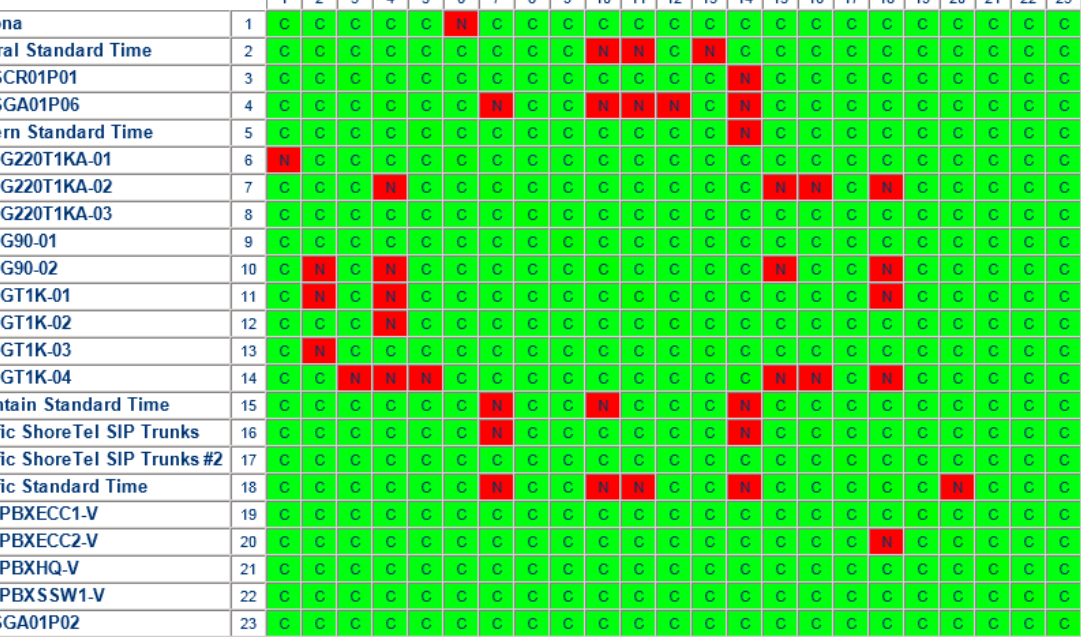
In the IRN definition press “Explain Shift” and then select the day you want to explore. The list will populate with all the Shifts that impact that IRN. Remember it does not matter if it is on your list! What matters is that the Shift exists for the ECC and you must specify an action, or in the absence of a direction, the default destination for that IRN will be followed!