Time for a new Call Center?
Recently we had the opportunity to move a major enterprise call center from a premise based solution to a virtual call center. Though the existing premise call center had performed faithfully for a number of years, we had lost faith in the manufacture and their reluctance to commit to a product road map that we could build on. Call Center technology changes as often as the weather and the demand for new features that the current system did not provide caused us to search for alternatives. Our client required advanced workforce and quality management including call recording, scoring and advanced reporting tools. Website integrations for visual IVR and “click to call”, Social Networking integration and SMS options were also high on our wish list. As the call center was expanding geographically we wanted a solution that did not require us to build a WAN to interconnect agents to a central server. We also wanted a company with a demonstrable track record, a rich history of experience and a customer reference list of others in our industry with similar deployment challenges.
We worked with our client to do the usual due diligence and explored both premise and cloud vendor solutions. The premise challenge was that the affordable architectures were basically centralized server applications. So if you had Agents in California, New York and London, you would have to network all your Agents back to wherever you put the contact center server. We have done literally hundreds of deployments these types of solutions, but in each case Agents would need to come up on a quality WAN network to be under the control of the contact center servers. CISCO has an excellent solution for geographically dispersed work groups with either the PCCE or UCCE. These are excellent call center solutions for mixed vendor ACD or geographically dispersed workgroups, but it would be more costly than the purchase of a used Russian ICBM missile. Additionally, the IT staff required to manage that caliber of deployment was more than our client was prepared to underwrite. Add in the ongoing cost of ongoing server refresh, system upgrades and other maintenance requirements we determined to focus on a “cloud” solution.
Clearing the Clouds!
When you focus on who has the experience, the references and the credibility to pull off a cloud based call center, the competitive playing field narrows quickly. Every vendor has learned to say “cloud” in the last couple of years, but who has really been executing customer focused call center solutions for more than 10 years? If you like the Gartner Group “magic quadrant” analysis, you will find about three players in the upper right hand quadrant. During our due diligence and RFQ process, two of the tree vendors in that quadrant changed their corporate identities through either merger or acquisition. This caused some concern on our part that as these new entities struggled to redefine themselves and the product lines that might result from their new combinations, we might be at the mercy of a company that was not yet fully formed!
In final analysis we chose to go forward with the Five9 solution and it has made all the difference!
Doing business the Five9 Way
They say “pre-sale” is about as good as it gets when it comes to vendor customer care. The Five9 team has set a new standard for both “pre-sales” and “post-sales” by which we will now measure every other vendor relationship going forward! Admittedly the Five9 “Enterprise Sales Director” we worked with was absolutely astonishing in meeting our requirements and exceeding our expectations. Always ready, prepared and available he never failed to deliver on a promise. We went through the normal “legal man and his bag full of deal killing goodies” back and forth between company attorneys, hammering out a Master Service Agreement but in the end both sides had come to an agreement that was fair and reasonable.
Five9 Project Implementation
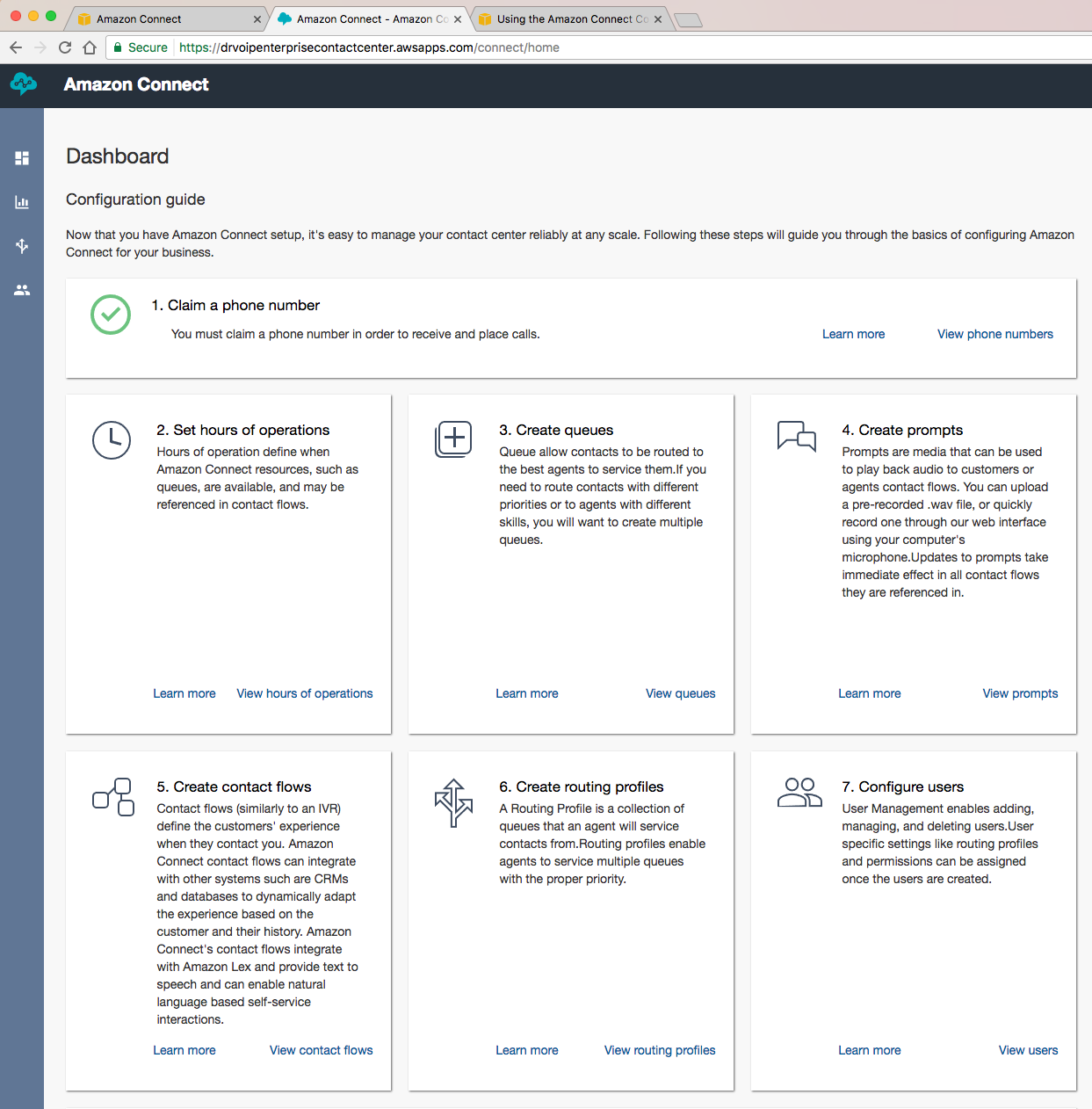
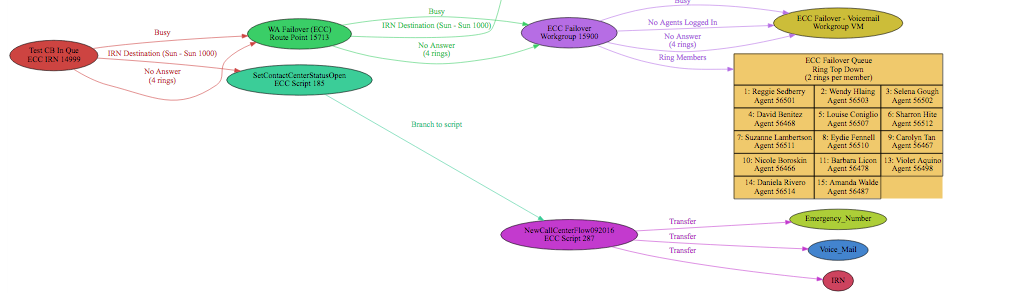
Five9 assigned a Project Manager, Platform Architect and Connection Manager within hours of signing a contract. We had network readiness test instructions and project workbooks almost immediately. Just as quickly we had access to the Five9 platform portal including DID numbers to build and test with while waiting for carriers to do the vaudeville act known as “porting”! We had a goal of having the Five9 solution replicate our existing call center as a project first phase and we set a goal of achieving “go live” within 90 days. As you would expect the Five9 team had a number of workbooks that needed to be completed. The existing call flow had to be documented, numbers assigned, agents and supervisors listed, MPLS circuit connectivity options ordered and database access requirements considered.
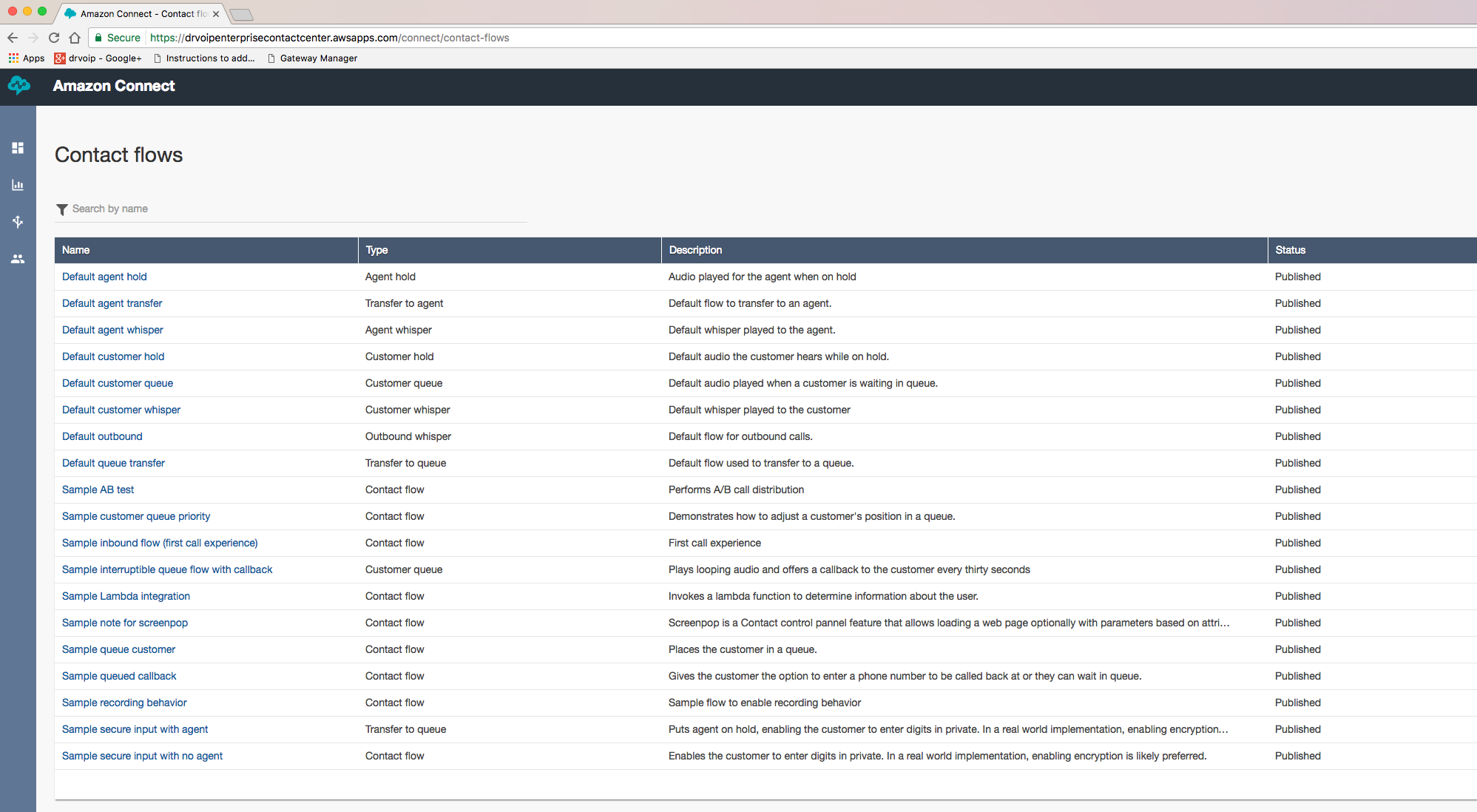
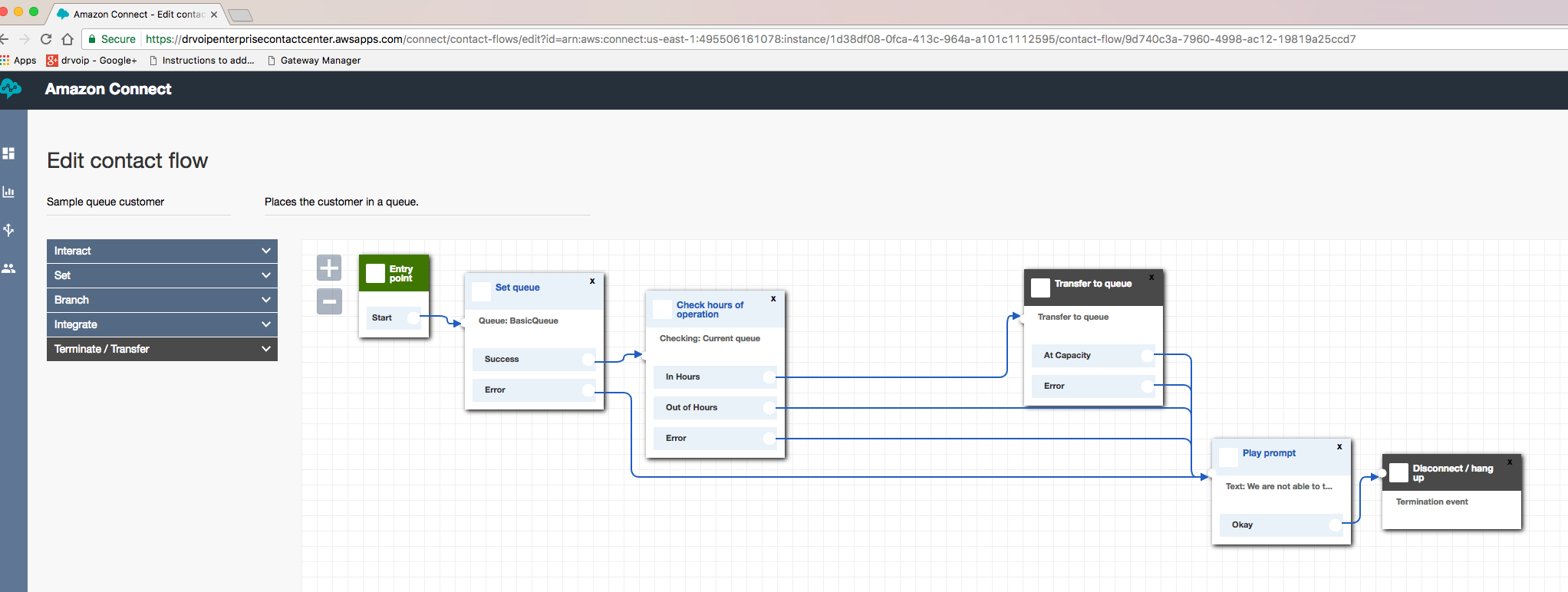
Most of us that have had to deploy large telecommunications projects know the drill. The bottleneck is always the client’s ability to get their homework assignments in on time! One of the early on challenges for this project was to replicate the CRM SQL database lookup we used for call routing decisions and agent screen pops on call arrival. When moving to a cloud solution the usual ODBC connector to the local server strategy was not going to work! We had to build out a web service front end to our SQL farm and not knowing the Five9 IVR scripting tool set gave us some concern. The fact of the matter was, that the Five9 scripting for IVR is as good or better than anything we have worked with historically and we think we have seen them all. Having never seen the solution before, it took about an 30 minutes for us to create an inbound campaign complete with audio prompts, agents profiles, screen displays and basic call flow. We were impressed with the breadth of functionality that could be created with the Five9 IVR scripting tools. Again, if you have deployed even a simple iPBX, you know that at “go live” you are still waiting for the client to record the auto attendant script! Five9 has a text to speech option that enable you to create prompts on the fly and worry about the professional voice artist later! The Platform engineer who actually implemented the solution, managed the webservice conversion from OBDC with style and grace. We had it operational and tested in no time!
The Five9 platform web portal has a rich library of training materials for administrators, supervisors and agents. Our call center supervisors were able to create agent profiles and add agents with the appropriate skills to new campaigns in no time. Actually, it was easier to log in to the portal and add the agents than it would be to list them in the workbook and dumping it on the implementation engineer! Agents could log in to the portal and take video training sessions that increase comfort, knowledge and reduced the jitters that come with any type of workplace change.
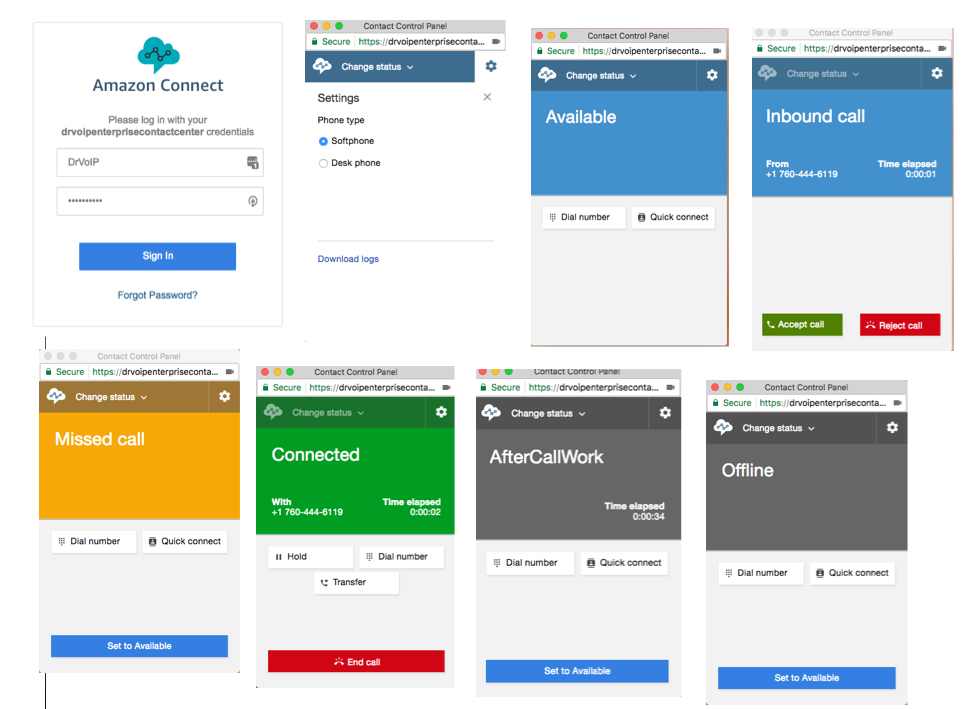
One of our early on decisions was to use the Agent Softphone rather than an actual handset. This meant that each Agent would have a workstation with a USB headset and no other phone hardware. While waiting out the usual 90 day carrier window for an MPLS link to both Five9 data centers in Santa Clara and Atlanta, we built a VPN tunnel to enable our aggressive “go live” target. In one location we had a VPN link, in the other we used a pure Internet connection. Truth be told the quality of the connection was so astonishing that we are no second guessing the MPLS requirement!
Virtual Contact Center “Go Live”
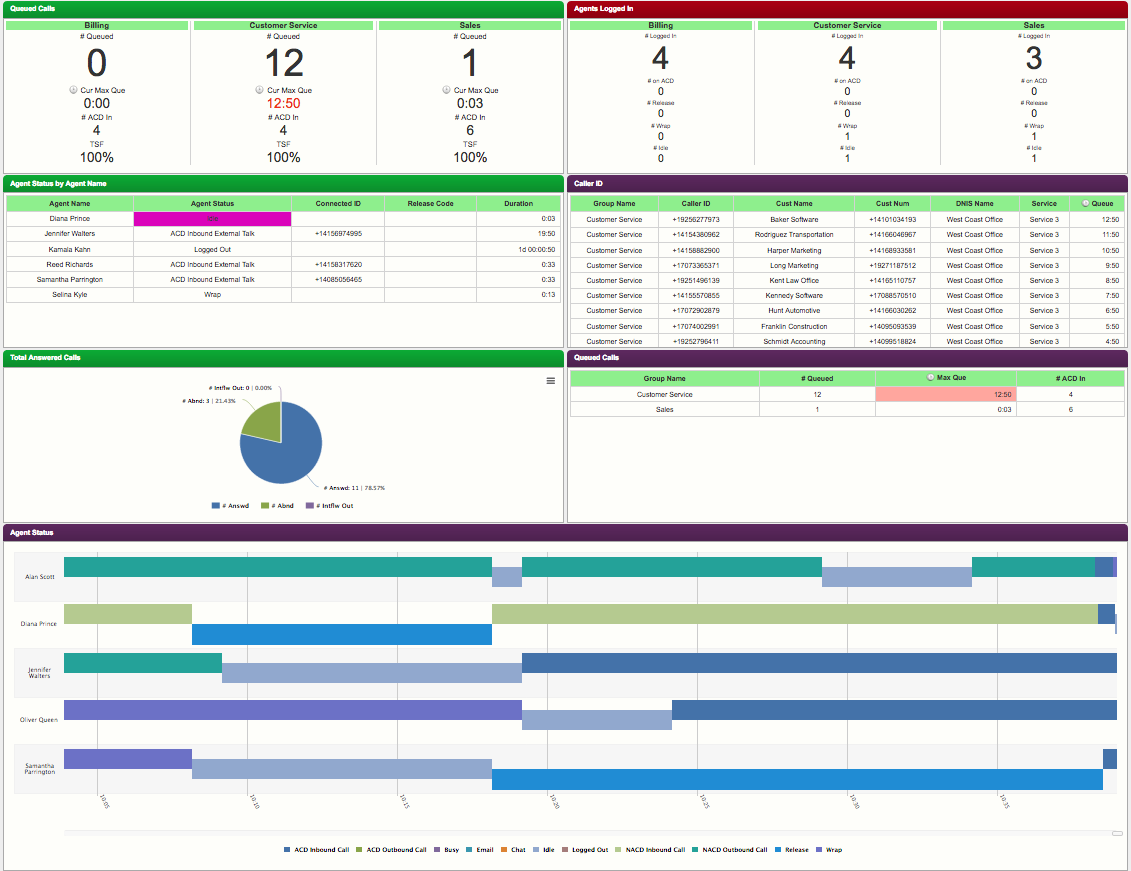
Again the quality of folks we worked with at Five9 was astonishing! This was most obvious at “go live”. We noted that several of the Five9 team members were at one time Five9 customers. These folks were so excited about the company, product and technology that they wanted to evangelize as employees! Our Project Manager and Solutions Architect were both former customers who now worked on the implementation team at Five9. We had multiple geographic locations for this deployment and the Five9 team showed up at 0500 at each location ready to work! Their knowledge and experience was a great part of the success of our launch as both Agents and Supervisors could benefit by the many operating hints this folks could provide. This call center is no sleeper, handling some 5K calls a day! The move to Five9 was painless and event free. We never lost a single call or skipped a beat in our normal daily operations!
Post “Go Live”
The Five9 project team began to transition the project to the customer service group. As part of this process a technical account representative was assigned to the project. This individual would be available to us for some number of hours a month to work with us on new campaigns and smooth any transition issues. So far, all has been better than expected and the experience and overall implementation has been excellent. We are now moving into the second phase of the deployment, something we will tackle internally as the tools and resources to do so have all been provided by Five9 expertise. We are looking forward to implementing a Salesforce connector; integrating the corporate website with a visual IVR component and getting the outbound campaign process cranked up.
Cloud Contact Center Advantages
Some of the advantages we have found moving the call center to the “cloud” are benefits of virtual call centers in general:
- Elastic scalability, pay as you go.
- Geographic Independence – Agents can be located anywhere that they have access to the Internet. Think Business Continuity and disaster recovery.
- Cost Allocation – Most call center expense is embedded in the general budget, with a VCC your costs are easily identified including call costs in real time.
- Media Traffice off the WAN – Calls to the VCC are over the PSTN and not over your internal VoIP network.
- Browser based Call Control – It is no longer necessary to push configuration files to desktops. This also enable desktop OS independence. Mac, Windows, Citrix whatever.
- Freedom from and endless cycle of software maintenance, upgrades, server and desktop refresh.
Cloud Transition Assitance
DrVoIP has been deploying VoIP solutions with a core competency in geographically dispersed Enterprise Contact Centers since 1998! We have worked with most of the solutions in the market place and regularly implement custom contact center software and scripting services for ShoreTel, CISCO and Calabrio. If you are considering a cloud based virtual call center, give us an opportunity to assist you with RFQ, vendor selection, design, deployment management and custom software integration. Our experience is global, our expertise is verifiable, our projects are on schedule and always exceed expectations! – DrVoIP