What is a route or dial plan?
Most if not all phone systems provide for route plans and calling or “class of service” privileges. The dial plan defines the over all numbering system used through out the system. For example, how many digits do we need to define all of our extension number or telephone endpoints? What access code do we use to indicate we want an outside line? What numbers will we set aside for system features like the automated attendant, voice mail, contact center and conference servers? Generally this is one of the first decisions you make when designing a new phone system. Once set, it is usually very cumbersome to alter or refine.
Calling privileges or “class of service” defines what facilities a specific user might have access to. For example, we might want the Lobby and Kitchen phones to be able to dial 911 and make internal calls, but we might restrict them from dialing outside numbers at all, let alone long distance or international phone calls. Some systems even restrict internal extensions from calling other internal extension numbers. For example you might isolate the CEO from being dialed by the automated attendant “dial by name” directory and you certainly do not want the over head paging system accessible by an outside caller!
How do we include a new branch with the same internal Extension numbers?
These options become increasingly more complex as organizations redefine themselves as a result of a merger or acquisition. How do you add that new branch office into the company phone system? Things become even more exciting when the new office has a “dial plan” that uses the same internal extension numbers already in use by the HQ phone system. ShoreTel and CISCO tackle this in very different ways and it is interesting to note the different strategies.
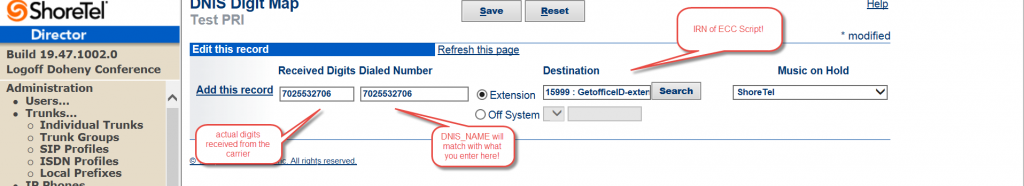
In ShoreTel you define you “dial plan” as the necessary first step in designing the phone system. How many digits do we need to dial internal telephone numbers? Out of the box, ShoreTel assumes you want to use three digit extension numbers. You can change them to four, five or more digits but you can only do this once. You can increase extension digit length but you can not reduce them, so plan carefully! The next issue is what range will we use for extension numbers? Will they start with 1, 2 or some other digit? Don’t forget those “system extensions” as you will need them for many features and system resources.
ShoreTel also uses the concept of a User Group and a Class of Service. A user group might be a function like Executive, Manager, Employee and House phones. The Class of service defines Telephone Features, Calling privileges and Mailbox options. Telephone features might include who can access the Intercom, or record their own phone calls. Calling privileges enable internal, local and long distance dialing options. Finally mail box options indicate the size of messages, greetings and administrative controls.
ShoreTel has a very simple to implement and understand concept for dialing plans and calling privileges. With simplicity, however, comes some restrictions. Lets take the example of acquiring a new business unit and they have an existing dial plan that conflicts with the one already in place. Well, you could through the inplace phone system out and install ShoreTel at that location (certainly the ShoreTel re-sellers plan) by expanding the existing ShoreTel but that would certainly mean an change in extension numbers at the newly acquired business unit. Optionally, you could install another ShoreTel system and integrate the two separate system through a SIP tie-trunk. Using a digit translation strategy you could let the other guys keep there old extension numbers but you would have two separate telephone systems, each with their own configuration database. (In CISCO parlance that would be a two “cluster” solution).
ShoreTel Simple or CISCO Complex?
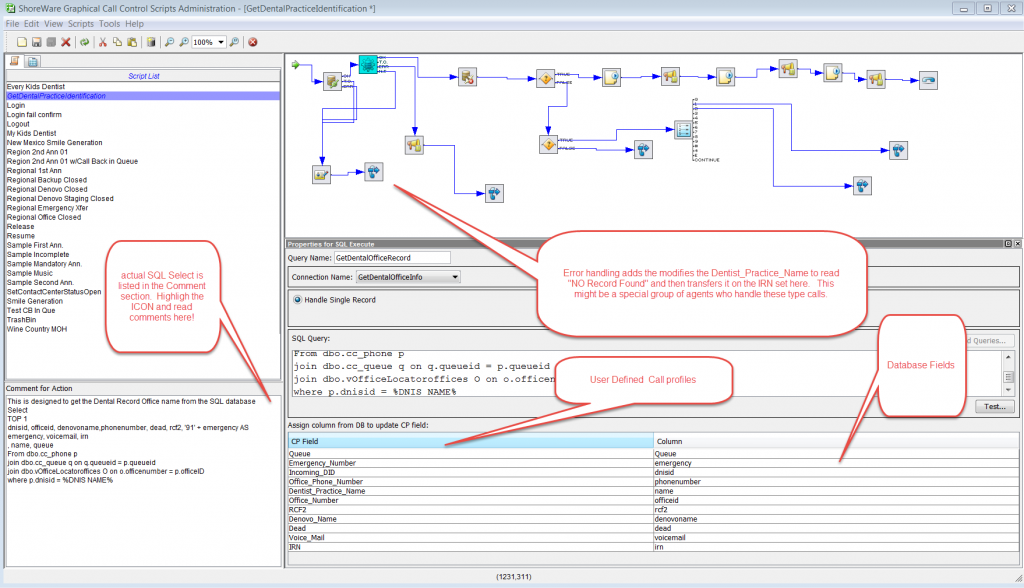
CISCO uses the concept of “route patterns” to define a dial plan. It is a bit more complex, but with that complexity comes great flexibility. A “route pattern” is a map for taking the digits a user dials and searching a database to find the route those digits should follow to complete the call. For example, a user in the California Office might dial 9,1-212-523-51234 to reach extension 234 in the New York office. The route pattern would then hit route list that might include a local PRI for a long distance call to NY, dropping the 9 and out dialing the E164 1+area code and number. That route list might also include a WAN gateway that directly terminates in NY and in that case, drops all the digits but the 234 while placing the call over the company’s WAN connection.
To be fair, ShoreTel can also complete a call over the WAN and would be smart enough to know that #234 also has a DID number of 212-523-51234. If the California user dialed #234, and the call could not be routed over the WAN, the call would be completed over the Long distance line using “PSTN fail over”. The feature does not, however work the other way. Had the user dialed the LD number and encountered a network busy condition, it could not then route the call over the WAN.
As to”class of service”, CISCO uses the concept of a “partition” and a “calling search space” (i.e. CSS). Though some folks like the “lock and key” metaphor, we think the best way to understand this is to realize that “partitions” define who can call me. “Calling Search Spaces” define who I can call. So if my line or phone is in a CSS that specifies partitions NYPhones, SFPhones, UKPhones, Windstream, COX and Verizon, then those are the objects I can call. If my device is in a partition named SFPhones and your CSS does not contain that Partition, then you can not call me.
Sounds a bit confusing, and at times it is. The structure however enables us to build some very significant solutions. Take that example in which you have phones with the same extension number in two different business units in the same “cluster” or phone system. You could put Extension 1234 in the NYPhones partition and in the SFPhones partition! They would not conflict with each other! Every phone, feature (i.e. intercom, conference), line in a CISCO deployment is in a specific “partition” and only reachable by an entity that has a Calling Search Space that includes that partition. Simple!
Given that we are not in the business of selling phone system, only engineering and supporting them, We do not have an emotional attachment to one over the other. We observe that ShoreTel is best suited for smaller deployments and in fact can be easily deployed and managed by a small business of 25 or more. Though there are larger ShoreTel deployments, we see them in the 100 – 1000 user line size most frequently. CISCO has a low end Solutions, the Business Edition 6K-S for system under 150 users, but the CISCO Collaboration solution could run a small a small country though the Business Edition 6K and 7K are optimized for 100 – 5000 users!
The video shows the two different approaches to solving these common route plan issues!